Fraud is one of the most pressing challenges in today’s digital and financial landscape. As online transactions and digital services continue to grow, fraudsters are constantly devising new ways to exploit security gaps, leading to severe financial losses and reputational harm. Whether targeting businesses, individuals, or financial institutions, fraudulent activities can disrupt operations, erode customer trust, and result in legal consequences.
So, what exactly is fraud, and how can it impact your business if you fall victim to it? In this article, we’ll explore the various types of fraud, their consequences, and the best strategies to protect yourself and your business. Stay informed and take proactive steps to mitigate risks in the ever-evolving digital world.
What is Fraud?
Fraud refers to deceptive practices intended to achieve financial or personal gain at the expense of another party. It takes multiple forms, each with distinct characteristics and methodologies.
In the digital age, fraud involves deceptive activities conducted online to steal money, personal information, or sensitive data. Common cybercrimes include phishing, identity theft, credit card fraud, and hacking. Fraudsters employ tactics such as fake emails, malicious websites, and social engineering to manipulate individuals into revealing their credentials.
They also exploit security vulnerabilities in financial systems, e-commerce platforms, and social media to carry out fraudulent activities. As digital transactions continue to grow, cybercriminals develop increasingly sophisticated techniques to bypass security measures and target unsuspecting users.
Common Types of Fraud
| Type of Fraud | Description |
| Account Takeover Fraud (ATO) | Cybercriminals gain unauthorized access to an individual’s account, allowing them to manipulate or steal sensitive information. |
| Transaction Fraud | Unauthorized financial transactions occur when stolen payment details are used to make illicit purchases or transfers. |
| Identity Theft | Fraudsters use stolen personal data to impersonate someone, applying for credit, loans, or services under false pretenses. |
| Phishing and Social Engineering | Scammers trick individuals into revealing confidential information through deceptive emails, calls, or websites. |
| Business Email Compromise (BEC) | Criminals pose as company executives to manipulate employees into sending money or confidential data. |
The Rising Cost of Fraud
The financial impact of fraud is staggering, with global losses reaching billions of dollars annually. It affects not only corporations but also individuals who fall victim to identity theft and financial scams. The consequences extend beyond monetary losses, posing significant risks to businesses and consumers alike:
- Financial Setbacks: Businesses face chargebacks, direct financial losses, and regulatory fines due to fraudulent activities.
- Reputational Damage: A single fraud incident can erode customer trust, leading to decreased sales and long-term brand harm.
- Legal and Compliance Risks: Companies that fail to prevent fraud may face lawsuits, regulatory scrutiny, and hefty penalties for non-compliance with data protection laws.
By understanding these risks, businesses and individuals can take proactive steps to strengthen fraud prevention and minimize potential losses.
How Fraudsters Stay Ahead

Fraudsters are always evolving their methods, making it challenging for businesses to keep up. Some of the latest fraudulent tactics include:
- Deepfake Technology: AI-generated identities make it difficult to distinguish real users from fraudsters.
- Synthetic Identity Fraud: Criminals create fake personas using a mix of real and fabricated information.
- Malware and Ransomware Attacks: Hackers use malicious software to gain control of systems and demand ransoms.
- Credential Stuffing: Fraudsters exploit stolen username-password combinations to breach multiple accounts.
Why Is Fraud Prevention More Important Than Ever?
As more financial services move online, fraudsters are finding new ways to exploit security gaps. Businesses that don’t take fraud prevention seriously risk losing customer trust, as people expect their personal and financial information to be protected. A single security breach can push customers away and damage a company’s reputation. On top of that, many governments enforce strict regulations on fraud prevention, requiring businesses to meet industry standards to avoid penalties.
Fraud can also disrupt daily operations, taking up valuable time and resources to investigate and resolve issues. This can slow down business growth and impact revenue. By prioritizing fraud prevention, companies can create a safer environment for customers, maintain compliance, and ensure smooth operations. In today’s digital world, staying ahead of fraud is essential for long-term success.
Indonesian Law on Fraud Prevention
In Indonesia, regulatory authorities have introduced stringent guidelines to combat fraud in financial institutions. The Indonesian Financial Services Authority (OJK) has enacted POJK 12 Tahun 2024, which mandates anti-fraud strategies for financial organizations.
Key Requirements of POJK 12 Tahun 2024:
- Strengthening internal controls to detect fraudulent transactions.
- Enhancing digital identity verification methods.
- Implementing fraud risk assessments and early warning systems.
For businesses operating in Indonesia, compliance with this law is crucial to avoiding penalties and maintaining trust within the financial ecosystem.
Benefits of Fraud Prevention
Implementing fraud prevention strategies offers several key advantages:
Implementing effective fraud prevention strategies provides several key advantages for businesses and individuals:
- Enhanced Security – Protects sensitive information and reduces the risk of data breaches.
- Stronger Customer Relationships – Builds trust by ensuring a safe and secure transaction environment.
- Operational Efficiency – Minimizes disruptions caused by fraud investigations, allowing businesses to focus on growth.
- Regulatory Compliance – Helps businesses meet legal and industry standards, avoiding penalties and legal issues.
- Reduced Chargebacks and Fraudulent Claims – Lowers financial losses by preventing unauthorized transactions and scams.
By prioritizing fraud prevention, businesses can safeguard their assets, strengthen customer confidence, and maintain long-term stability.
Challenges in Fraud Prevention
While fraud prevention is essential, businesses face multiple obstacles when implementing these measures:
Keeping Up with Evolving Fraud Techniques – Cybercriminals are constantly innovating, requiring businesses to stay ahead.
Balancing Security and User Experience – Excessive security checks can create friction for legitimate users.
Cost of Implementation – Advanced fraud detection systems require investment in technology and training.
Data Privacy Concerns – Striking a balance between security and customer privacy is crucial.
Fraud Prevention Solutions by Sumsub
Sumsub offers a comprehensive suite of fraud prevention solutions that help businesses protect against identity fraud, account takeovers, and unauthorized access. By leveraging advanced technologies like AI-driven verification and behavioral analytics, these solutions enhance security while maintaining a seamless user experience.
1. Email and Phone Verification
One of the fundamental methods to mitigate fraud is verifying a user’s contact details, such as email addresses and phone numbers. This process helps assess the risk associated with a particular user and detect potentially fraudulent behavior. Sumsub’s verification technology evaluates various risk factors, including:
- Disposable or Temporary Emails: Identifies whether an email is from a suspicious domain or a disposable email provider.
- Phone Number Risk Assessment: Detects virtual, VoIP, or blacklisted numbers often associated with fraud.
- Geo-Location and IP Analysis: Matches the phone number’s country code with the user’s provided location to detect inconsistencies.
- Previous Fraud Patterns: Cross-checks against global fraud databases to flag users with a history of suspicious activity.
By implementing this verification method, businesses can prevent fraudulent account creation and ensure a higher level of trust within their systems.
2. Account Takeover (ATO) Prevention
Account Takeover (ATO) is a growing threat where cybercriminals gain unauthorized access to user accounts, often leading to financial loss or data breaches. Sumsub combats ATO fraud using a multi-layered security approach that includes:
- Behavioral Analytics: Tracks user behavior, such as typing speed, mouse movement, and browsing patterns, to detect anomalies that may indicate fraud.
- Biometric Authentication: Uses facial recognition or fingerprint scanning to confirm a user’s identity and prevent unauthorized logins.
- Real-Time Risk Assessment: Analyzes login attempts, device information, and session history to identify suspicious activity, triggering alerts or additional verification steps when necessary.
- Two-Factor Authentication (2FA) Enforcement: Encourages or mandates the use of 2FA to add an extra layer of protection against unauthorized access.
With these techniques, businesses can safeguard user accounts and reduce the risk of ATO attacks.
3. Short Video Fragment Verification
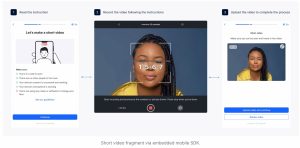
To enhance identity verification and fraud prevention, Sumsub integrates short video fragment verification, an AI-driven technology that ensures user authenticity. This method requires users to submit a brief video clip instead of relying solely on static images or documents. Key features include:
- Liveness Detection: Identifies whether the person in the video is real and present at the moment of submission, preventing deepfake or spoofing attempts.
- Facial Recognition Matching: Compares the submitted video with official identity documents to verify authenticity.
- AI-Powered Anomaly Detection: Detects inconsistencies, such as manipulated videos, pre-recorded footage, or synthetic identities.
- Real-Time Decision Making: Provides instant verification results, allowing businesses to approve or flag users quickly.
Contact Q2 Today to Secure Your Business
For expert guidance and tailored fraud prevention solutions, reach out to Q2 today and take the first step toward a secure, fraud-free future.
Don’t let fraud compromise your business! With Sumsub’s One-Verification Platform, you can streamline onboarding, enhance due diligence, and prevent fraud efficiently. From email and phone verification to short video fragment authentication, our cutting-edge technology ensures trust, security, and compliance.
Author: Ary Adianto
Content Writer CTI Group

